The Rocke group is using a new piece of cryptojacking malware dubbed Pro-Ocean to target Apache ActiveMQ, Oracle WebLogic, and Redis installs.
The cybercrime group Rocke is using a new piece of cryptojacking malware called Pro-Ocean to target vulnerable Apache ActiveMQ, Oracle WebLogic, and Redis intalls.
The malware is an evolution of a Monero cryptocurrency miner that was first spotted by Unit 42 researchers in 2019.
The new malware implement new and improved rootkit and worm capabilities, it continues to target cloud applications by exploiting known vulnerabilities such as Oracle WebLogic (CVE-2017-10271) and Apache ActiveMQ (CVE-2016-3088) servers.
“Pro-Ocean uses known vulnerabilities to target cloud applications . In our analysis, we found Pro-Ocean targeting Apache ActiveMQ (CVE-2016-3088), Oracle WebLogic (CVE-2017-10271) and Redis (unsecure instances).” reads the analysis published by Palo Alto Networks. “In the case that the malware runs in Tencent Cloud or Alibaba Cloud, it will use the exact code of the previous malware to uninstall monitoring agents to avoid detection.”

Before installation, Pro-Ocean also attempts to remove other malware such as Luoxk, BillGates, XMRig and Hashfish. Once installed, the malicious code attempts to kill any process that heavily uses the CPU.
The installation script is written in Bash and is obfuscated, it is used to conduct multiple tasks that prepare the system for the deployment of the Pro-Ocean miner. The analysis of the code revealed that it was specifically designed to target cloud applications, among its targets there are Alibaba Cloud and Tencent Cloud.
Below the list of tasks carried out by the scripts:
- Attempt to remove other malware and miners (e.g. Luoxk, BillGates, XMRig, and Hashfish).
- Erase all of the cron tasks that could have been set up by other malware.
- Disable the iptables firewall so that the malware will have full access to the internet.
- In the case that the malware runs in Tencent Cloud or Alibaba Cloud, it will use the exact code of the previous malware to uninstall monitoring agents to avoid detection.
- Look for SSH keys and attempt to use them in order to infect new machines.
To avoid detection, the cryptocurrency Monero miner uses the native Linux feature LD_PRELOAD.
“LD_PRELOAD forces binaries to load specific libraries before others, allowing the preloaded libraries to override any function from any library. One of the ways to use LD_PRELOAD is to add the crafted library to /etc/ld.so.preload.” continues the analysis.
Pro-Ocean deploys an XMRig miner 5.11.1 to mine Monero, unlike 2019 variant, it uses a Python infection script to implement “wormable” capabilities.
This script retrieves the IP public address of an infected machine by querying the online service “ident.me,” then attempts to infect all the machines in the same 16-bit subnet (e.g. 10.0.X.X). The malicious code tries to execute public exploits against each machine in the subnet.
Upon successfully exploiting the above vulnerabilities, the Python script delivers a payload that downloads another script that fetches the Pro-Ocean from a remote HTTP server.
Palo Alto Networks researchers believe threat actors could expand the list of vulnerabilities to exploit to target the larger number of cloud applications as possible.
Rocke Group has been active at least since 2018 by Cisco Talos, their cryptomining operations have evolved over time with new feature and evasion techniques.
“Cryptojacking malware targeting the cloud is evolving as attackers understand the potential of that environment to mine for crypto coins. We previously saw simpler attacks by the Rocke Group, but it seems this group presents an ongoing, growing threat. This cloud-targeted malware is not something ordinary since it has worm and rootkit capabilities.” concludes the report. “We can assume that the growing trend of sophisticated attacks on the cloud will continue.”
If you want to receive the weekly Security Affairs Newsletter for free subscribe here.
(SecurityAffairs – hacking, Pro-Ocean)
Share On
Pierluigi Paganini
Pierluigi Paganini is member of the ENISA (European Union Agency for Network and Information Security) Threat Landscape Stakeholder Group and Cyber G7 Group, he is also a Security Evangelist, Security Analyst and Freelance Writer. Editor-in-Chief at “Cyber Defense Magazine”, Pierluigi is a cyber security expert with over 20 years experience in the field, he is Certified Ethical Hacker at EC Council in London. The passion for writing and a strong belief that security is founded on sharing and awareness led Pierluigi to find the security blog “Security Affairs” recently named a Top National Security Resource for US. Pierluigi is a member of the “The Hacker News” team and he is a writer for some major publications in the field such as Cyber War Zone, ICTTF, Infosec Island, Infosec Institute, The Hacker News Magazine and for many other Security magazines. Author of the Books “The Deep Dark Web” and “Digital Virtual Currency and Bitcoin”.
The Rocke group is using a new piece of cryptojacking malware dubbed Pro-Ocean to target Apache ActiveMQ, Oracle WebLogic, and Redis installs.
The cybercrime group Rocke is using a new piece of cryptojacking malware called Pro-Ocean to target vulnerable Apache ActiveMQ, Oracle WebLogic, and Redis intalls.
The malware is an evolution of a Monero cryptocurrency miner that was first spotted by Unit 42 researchers in 2019.
The new malware implement new and improved rootkit and worm capabilities, it continues to target cloud applications by exploiting known vulnerabilities such as Oracle WebLogic (CVE-2017-10271) and Apache ActiveMQ (CVE-2016-3088) servers.
“Pro-Ocean uses known vulnerabilities to target cloud applications . In our analysis, we found Pro-Ocean targeting Apache ActiveMQ (CVE-2016-3088), Oracle WebLogic (CVE-2017-10271) and Redis (unsecure instances).” reads the analysis published by Palo Alto Networks. “In the case that the malware runs in Tencent Cloud or Alibaba Cloud, it will use the exact code of the previous malware to uninstall monitoring agents to avoid detection.”
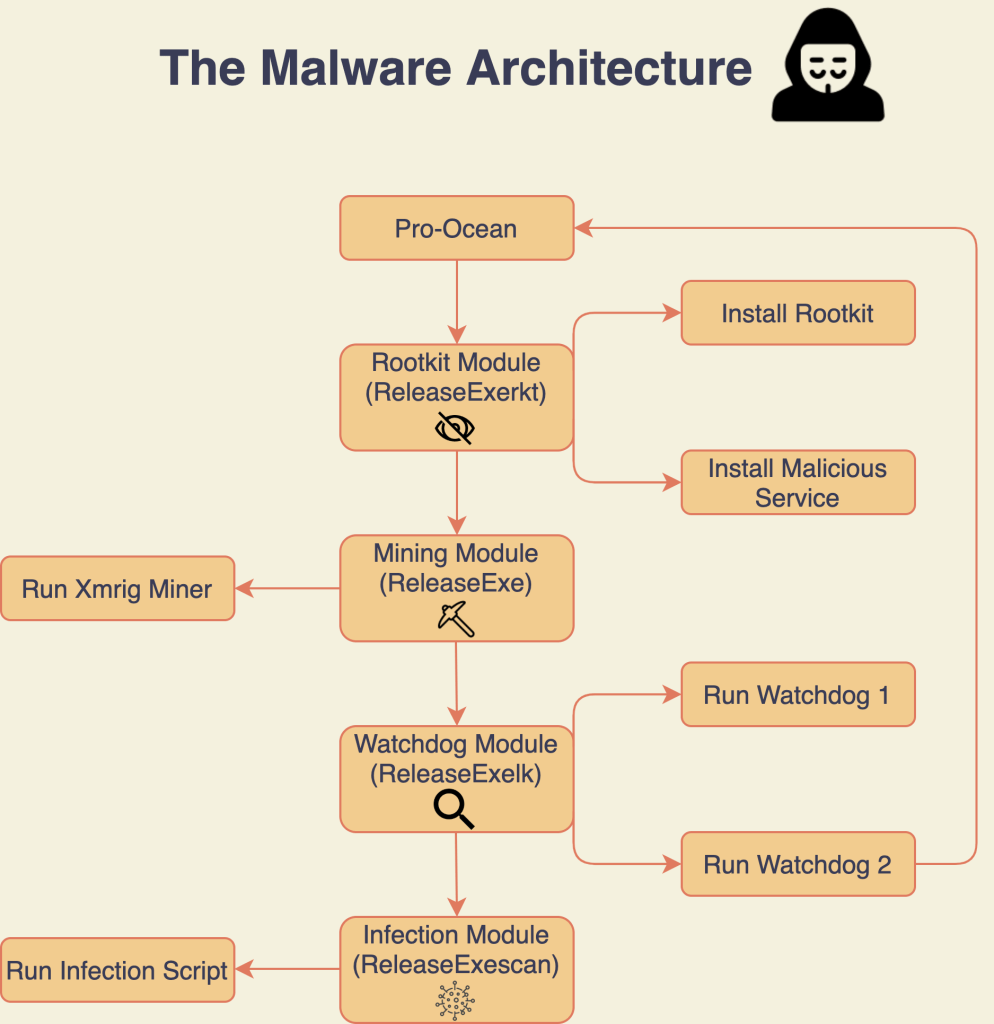
Before installation, Pro-Ocean also attempts to remove other malware such as Luoxk, BillGates, XMRig and Hashfish. Once installed, the malicious code attempts to kill any process that heavily uses the CPU.
The installation script is written in Bash and is obfuscated, it is used to conduct multiple tasks that prepare the system for the deployment of the Pro-Ocean miner. The analysis of the code revealed that it was specifically designed to target cloud applications, among its targets there are Alibaba Cloud and Tencent Cloud.
Below the list of tasks carried out by the scripts:
- Attempt to remove other malware and miners (e.g. Luoxk, BillGates, XMRig, and Hashfish).
- Erase all of the cron tasks that could have been set up by other malware.
- Disable the iptables firewall so that the malware will have full access to the internet.
- In the case that the malware runs in Tencent Cloud or Alibaba Cloud, it will use the exact code of the previous malware to uninstall monitoring agents to avoid detection.
- Look for SSH keys and attempt to use them in order to infect new machines.
To avoid detection, the cryptocurrency Monero miner uses the native Linux feature LD_PRELOAD.
“LD_PRELOAD forces binaries to load specific libraries before others, allowing the preloaded libraries to override any function from any library. One of the ways to use LD_PRELOAD is to add the crafted library to /etc/ld.so.preload.” continues the analysis.
Pro-Ocean deploys an XMRig miner 5.11.1 to mine Monero, unlike 2019 variant, it uses a Python infection script to implement “wormable” capabilities.
This script retrieves the IP public address of an infected machine by querying the online service “ident.me,” then attempts to infect all the machines in the same 16-bit subnet (e.g. 10.0.X.X). The malicious code tries to execute public exploits against each machine in the subnet.
Upon successfully exploiting the above vulnerabilities, the Python script delivers a payload that downloads another script that fetches the Pro-Ocean from a remote HTTP server.
Palo Alto Networks researchers believe threat actors could expand the list of vulnerabilities to exploit to target the larger number of cloud applications as possible.
Rocke Group has been active at least since 2018 by Cisco Talos, their cryptomining operations have evolved over time with new feature and evasion techniques.
“Cryptojacking malware targeting the cloud is evolving as attackers understand the potential of that environment to mine for crypto coins. We previously saw simpler attacks by the Rocke Group, but it seems this group presents an ongoing, growing threat. This cloud-targeted malware is not something ordinary since it has worm and rootkit capabilities.” concludes the report. “We can assume that the growing trend of sophisticated attacks on the cloud will continue.”
If you want to receive the weekly Security Affairs Newsletter for free subscribe here.
(SecurityAffairs – hacking, Pro-Ocean)




