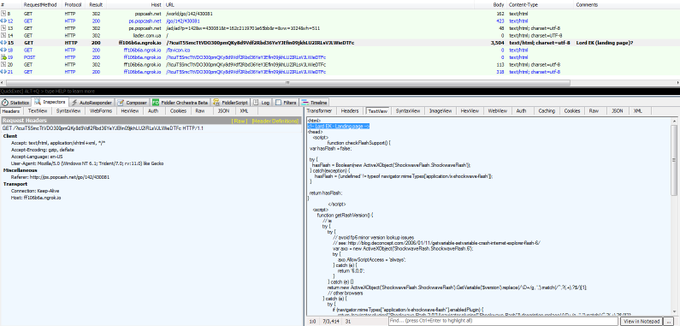
A new kit for web-based attacks calling itself Lord EK has been spotted at the beginning of the month as part of a malvertising chain that uses the PopCash ad network.
The exploit kit (EK) leverages a use-after-free vulnerability in Adobe Flash and relies on the ngrok service that can set up a secure connection to expose to the internet local servers behind NATs and firewalls.
Work in progress
Discovered by Virus Bulletin researcher Adrian Luca at a time when it was still under development, Lord EK was named so because of a landing page that carried this tag.
The kit’s initial payload was njRAT, an old remote access trojan with early variants traced to November 2012 and preferred by Nigerian scammers running business email compromise (BEC) attacks.
A researcher noticed that Lord EK then switched to version 2.0.3 of ERIS, a piece of ransomware delivered in the past by other exploit kits such as RIG and Azera.
According to research from Jérôme Segura of Malwarebytes, the kit uses a compromised website for redirecting to a landing page and it is part of a malvertising chain that uses the PopCash ad network.
The exploit is pushed by a function that first checks for the presence of Flash Player and its version. The second part of the code in the landing page gathers details about the Flash version used on the host ad geo-location attributes about the victim.
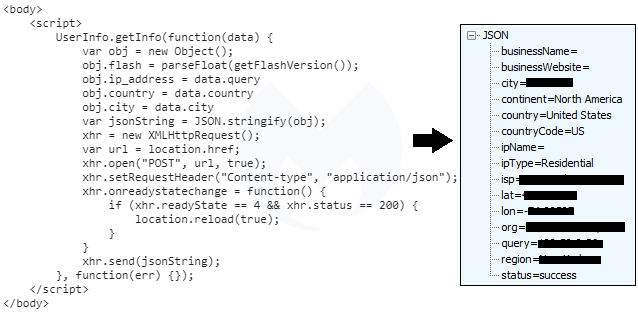
The vulnerability was used as a zero-day in an APT attack against the Russian FSBI “Polyclinic #2” medical clinic. Adobe patched it in December 2018 but the exploit was quickly adopted by multiple exploit kits, including Spelevo.
After exploitation, Lord EK redirects the victim to the Google home page, Segura notes, adding that this behavior was also observed with Spelevo.
With Flash set to die at the end of 2020, exploit kits may soon dwindle into extinction themselves. However, the author of Lord EK seems to be actively tweaking the kit, says Segura.
“Even though the vulnerabilities for Internet Explorer and Flash Player have been patched and both have a very small market share, usage of the old Microsoft browser still continues in many countries.” – Jérôme Segura
Related Articles:
Ransomware: Most Popular Malware in Underground Forums
Rig Exploit Kit Pushing Eris Ransomware in Drive-by Downloads
New Exploit Kit Spelevo Carries Bag of Old Tricks
Sodinokibi Ransomware Now Pushed by Exploit Kits and Malvertising
Bleeping Computer® is a community of individuals of all ages who are here to learn new information, to help each other, and to help their fellow peers. With that in mind, we ask that all members please follow these simple rules in order to create an atmosphere where everyone feels comfortable.
The rules are as follows:
- All information and instructions given within these forums is to be used at your own risk. By following or using any of this information you give up the right to hold BleepingComputer.com liable for any damages.
- All the forums are categorized by topics. Please post your questions or messages in the appropriate forum.
- Answers to many of the questions you may have can be found in the Tutorials Section, Glossary, or from other posts on the message boards. Please use the search functions, at the top right of each page, to find your answers. If you are still having problems, feel free to post your question.
- All help must be provided in the forums or on our Discord Server. We do not allow support to be provided or requested via personal message, email, or remote desktop control programs (Logmein, TeamViewer, etc).
- If a topic is posted in a forum that is not appropriate for the question, the staff has the right to move that topic to another better suited forum.
- The posting of any copyrighted material on our web site is strictly prohibited.
- Posting links in order to generate affiliate commissions is not permitted at BleepingComputer.com. Any posts that are deemed to be posted in order to generate affiliate commissions, regardless of the product being promoted, will be deleted. If a user continues to create affiliate SPAM posts, they will be banned.
- Posting links to non-Bleeping Computer malware removal guides is NOT permitted with the exception of security vendors who sometimes release specialized tools and instructional documentation. This is because it is impractical for BleepingComputer to monitor and review all such guides for accuracy, no matter how accurate those guides may, in fact, be.
- There will be no use of profanity on our message boards. This will not be tolerated and can lead to immediate suspension.
- When posting, please use proper grammar. Refrain from ‘text-message’ style substitutions of words like ‘u’ for ‘you’, and ‘ur’ for ‘your’. This is a multi-national forum, and some of our non-english speaking members must use translation software which is confused by abbreviations. Most of our volunteer members are very busy helping as many people as they can, and a post that is hard to read will often be overlooked.
- There will be no racial, ethnic, gender based insults or any other personal discriminations. This will not be tolerated and can lead to immediate suspension.
- There will be no posts meant to offend or hurt any other member, in a manner which is offensive or inflammatory. This includes flaming or instigating arguments.
- Spamming is not permitted; please keep all your posts as constructive as possible.
- Pornography, warez, or any other illegal transactions may NOT be linked in any shape or form.
- If you have questions regarding homework, we will only help you with general concepts. If you are looking for a complete solution or answer, we will most likely just delete your post.
- No subject matter will be allowed whose purpose is to defeat existing copyright or security measures. If a user persists and/or the activity is obviously illegal the staff reserves the right to remove such content and/or ban the user. This would also mean encouraging the use or continued use of pirated software is not permitted, and subject to the same consequences.
- If you are receiving assistance in the Virus Removal forum, you are not allowed to request assistance for the same computer at another malware removal forum. This is to prevent conflicting advice from causing issues with your computer or making it unbootable.
- This forum has the right to request alteration or deletion of any offensive post. If this is not done in a prompt manner, the Staff will delete the material themselves.
- Posts may be deleted for any reasons the forum administrators deem reasonable.
- Pictures may be posted as long as they are not explicit, offensive, or copyrighted.
- Advertisements, of any sort, are not permitted. This includes member names and links to commercial sites in Signatures, or in posts. You also may not solicit sales for Newegg through the use of promotion or coupon codes. If you would like to advertise on our site, contact us here.
- In order to reduce spam on the site, you will not be able to add a signature to your account until you reach 25 posts. Signatures are limited to 5 lines or 2000 characters; whichever comes first. If your signature is larger than the allotted size given or deemed unacceptable, you will be requested to adjust your signature. Failure to comply will result in the removal of your signature.
- Only one image per signature. Images in signatures must also be no larger than 500 pixels wide X 90 pixels high. If you have more than one image you will be requested to remove one. If this is not done in a timely manner the staff has the right to modify your signature to abide by these rules.
- Any links in signatures or profiles cannot be commercial in nature or they will be removed by BleepingComputer. You may not put links in your signature soliciting donations unless you are in certain member groups. Those member groups that are allowed will be expressly notified. If you have a personal website or off-site help resource, that is more than fine, but you can not sell products or services through your signature. Multiple links to the same site, unless for a very specific reason, are not permitted in a signature and will be removed.
- Avatars must be in good taste. This means no vulgar or violent images, pornography, or profanity. Avatars that are found to be inappropriate will be removed at the discretion of the staff.
- Linking to hate, anti-Semitic, racist, pornography, warez, or other illegal sites is not permitted.
- Links in your signature must be unobtrusive and can not use formatting so that attention is brought to them.
- Member’s display names can not be email addresses. This rule is in place to protect you from spam bots who will pick up your email address and spam you.
- Members may have only one account on this forum. There is no need to have more than one.
- Any impersonation of a user from these forums, in any mode of communication, is strictly prohibited and will result in a banning.
- Linked and locked topics are pruned regularly to reduce page clutter. If you have a question about where your topic went, please PM a Moderator or Administrator before starting a new topic asking where it went, or posting a duplicate of the original topic. We will be happy to provide you with a link to the new location, or a reason why it was locked and/or removed.
Violation of any of these rules can lead to a banning of the user from our Web Site and a deletion of their account. The consequences will be determined by the Staff on a case by case basis.
When posting you agree that the administrators and the moderators of this forum have the right to modify, delete, edit or close any topic, signature, account, or profile data at any time that they see fit. If you have any questions concerning this, please do not start a new thread, but rather private message to an administrator or moderator.