
Security researchers analyzing the security flaws present in IoT devices used in smart buildings were able to replace the real video feeds with arbitrary footage.
As corporations act to reduce operational costs through automation provided by an ecosystem of connected devices, they also open up to security risks stemming from the configuration and management of the very IoT systems deployed to increase the overall efficiency of a building.
Legacy buildings relying on building automation systems (BAS) have been relying increasingly on IoT components available in consumer stores instead of the industry-specific modules that are both pricier and more difficult to get.
Easy installation and management of IoT components is attractive but often comes with the hazard of insecurity, most of the times because makers rush into marketing.
Insecure by default
Security researchers at Forescout set up a test environment that mimics a smart building’s integration of video surveillance (IP cameras), smart lighting (Philips Hue), and an IoT system designed to integrate components in other subsystems intended for services such as monitoring energy consumption and space utilization or predicting infrastructure maintenance needs.
During the reconnaissance stage, the researchers noticed that encrypted protocols for video streaming (SRTP, RTP over TLS), file transfer (SFTP) and web management (HTTPS) were either not supported or were not enabled by default.
One effect of this is a poor configuration of the device that allows “traffic sniffing and tampering, including sniffing credentials and sensitive information, including patient information in hospitals or video footage.”
Improper configuration and serious security vulnerabilities that are frequently uncovered in IoT devices are the weak spots an adversary could rely on to carry out an attack.
“Two of the cameras we purchased for the lab, with the latest firmware versions installed, were found critically vulnerable (by another company) a few weeks after we started our research.” – Forescout
Abusing insecure streaming protocols in IP cameras are not a difficult task for an attacker that is already on the network, an advantage that can be obtained without much effort (phishing, connecting a rogue device to the network).
Switching the video feed, Ocean’s 11 style
For the purpose of the demonstration, Forescout researchers used two types of attacks (denial of service and footage replay) that led to rendering an arbitrary stream to the video surveillance system (VSS).
The model and brand of the cameras products are irrelevant as long as they rely on insecure streaming protocols, which ensure transmission over the network.
The first stage of the attack is to create a denial-of-service condition on the VSS, which would prevent it from showing, recording, and storing footage from the camera.
The researchers achieved this by abusing the RTSP (Real-Time Streaming Protocol) or RTP (Real-time Transport Protocol) traffic.
“When the NVR tries to establish a connection with a camera, it issues a sequence of RTSP commands: OPTIONS, DESCRIBE, SETUP, and PLAY,” Forescout says.
If the attacker can interfere with these messages (dropping a command request, changing its destination, dropping a response), the NVR (network video recorder) will no longer be able to connect to the camera.
The same can be achieved for an RTP connection by dropping packets and thus forcing the NVR to terminate the current session.
By flooding the RTP connection by injecting packets, the attacker can obtain one of the following effects:
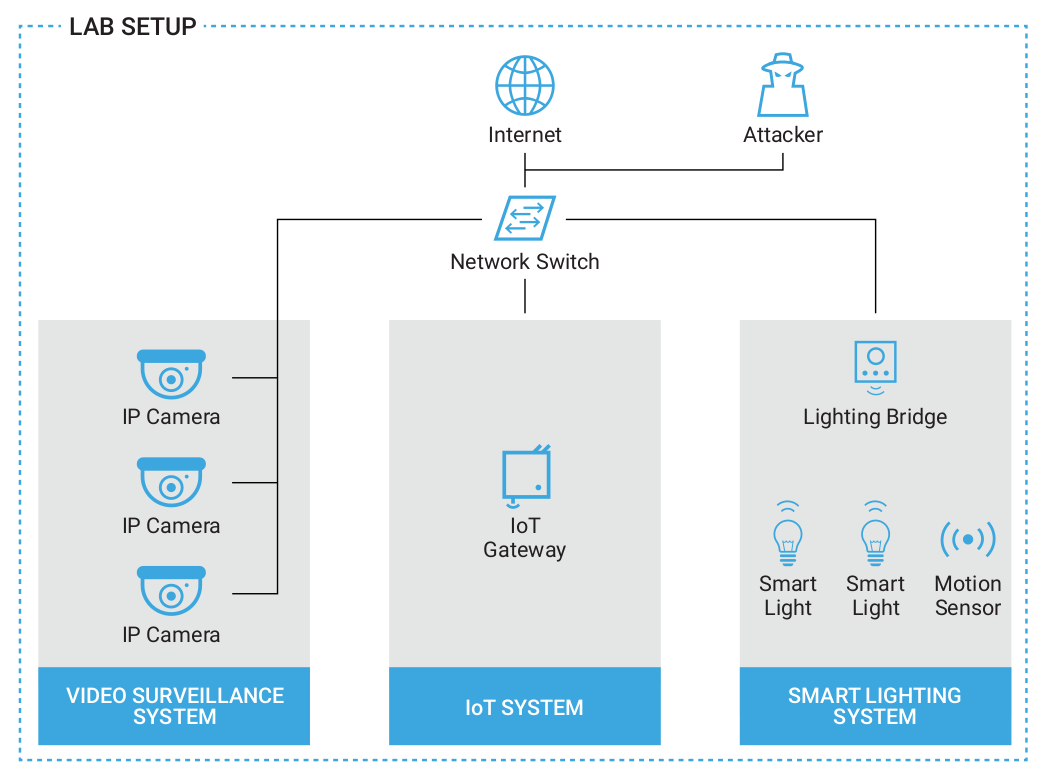
- A frozen image from the original footage is seen on the NVR
- The streamed footage from the attacker machine is seen on the NVR
- A green image is shown because both streams interfere with each other
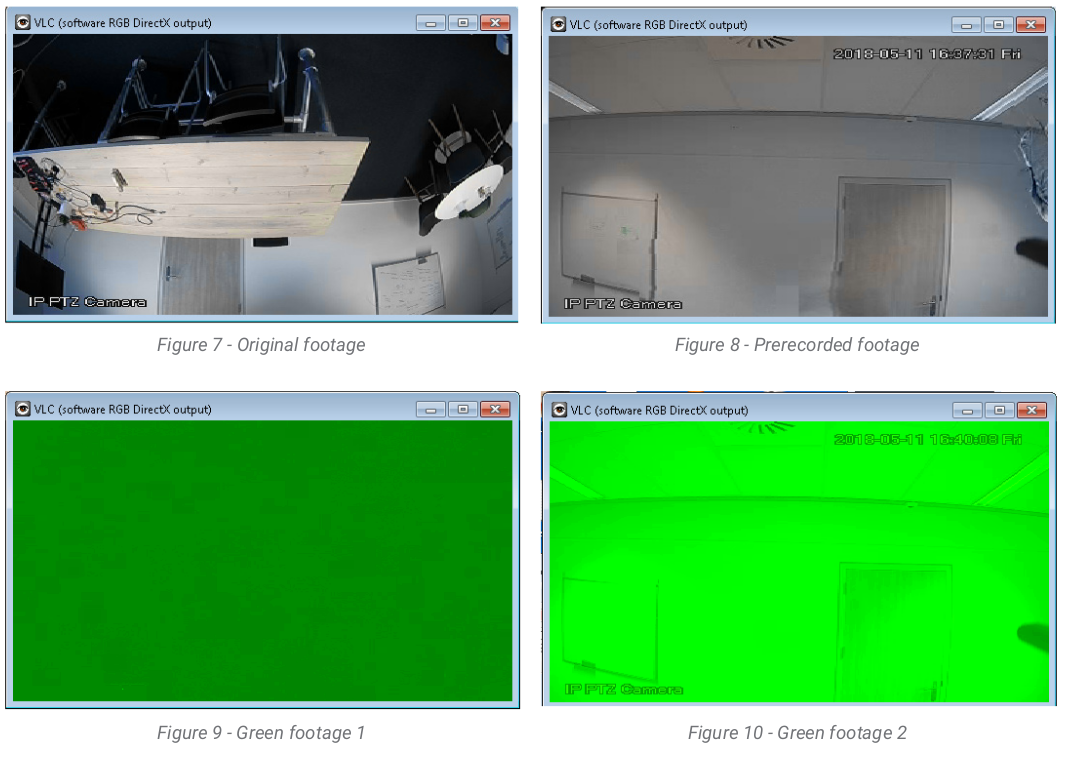
In the second stage of the attack, the adversary can force the NVR to render pre-recorded footage when the device tries to establish a new session following the DoS.
“When the NVR tries to establish a new session, capture the SETUP request and change the client port to a different one. This results in making the camera stream to the port specified by the attacker instead of the one initially requested by the NVR. After sending the PLAY command, the NVR will wait for traffic on the port which it specified in the SETUP request, but the camera will stream to a different port.”
The attacker has a limited window of opportunity to achieve this because the NVR will try to establish a new connection if it receives no traffic.
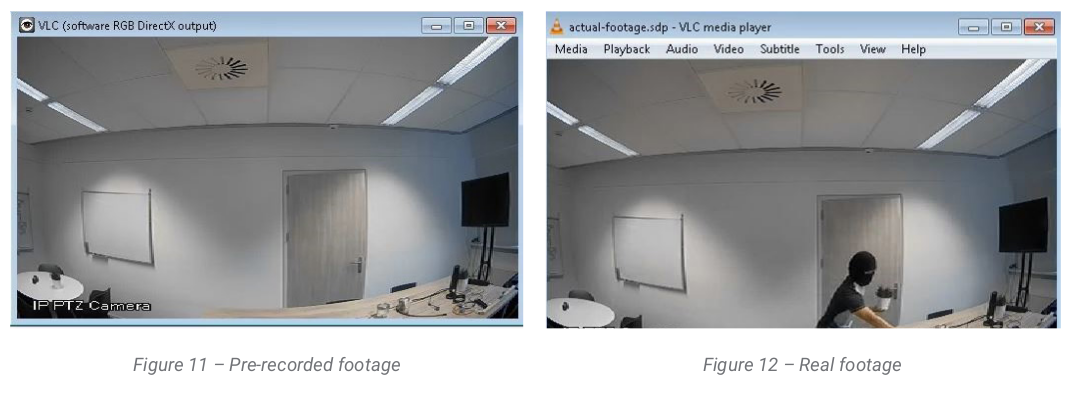
A video demonstration of attack is available here.
Looking on Shodan for potential targets, the researchers found over 4.6 million devices reachable over the internet with cleartext RTSP. Most of them are in China, the U.S. and Brazil.
Owning the lighting system
Forescout also tested how a threat actor could abuse the Philips Hue smart lighting system. As was the case with the VSS, the attack scenario considers an adversary with a rogue device on the network, a method often successful in penetration testing assignments.
One of the results was to disable the system via DoS, while another allowed reconfiguring the platform. This was possible by misusing an API that allows interaction with the lights using RESTful HTTP requests.
“Authentication in the API is handled by sending [in clear text], with every request, a token that is generated when a user registers with the bridge. Malicious access can be achieved either by sniffing the network and capturing the token of an existing user or by registering a new user.” – Forescout
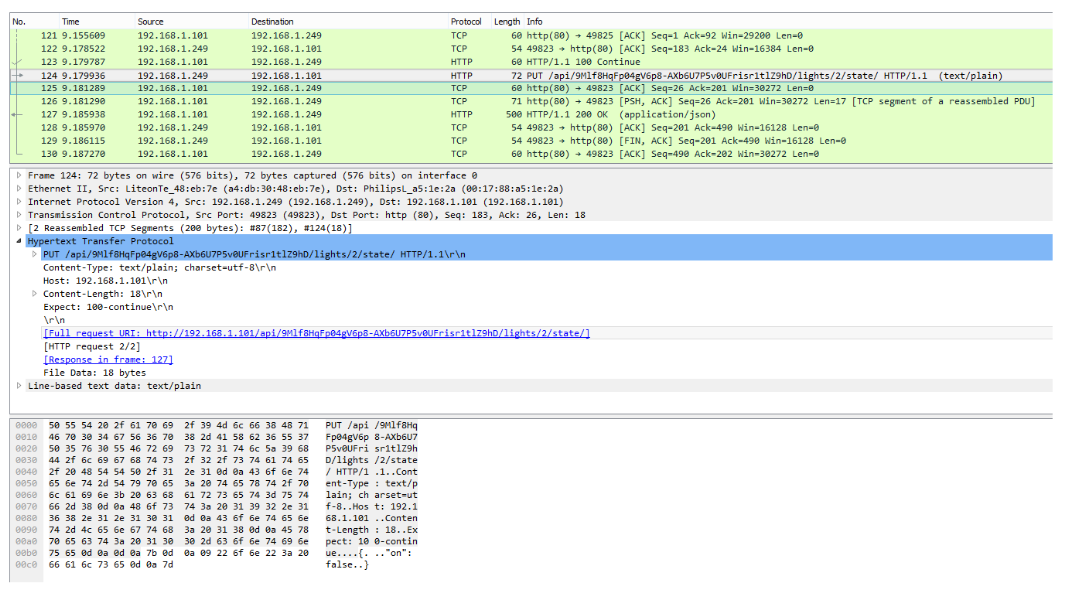
The method allows the adversary to switch off specific light bulbs, make them blink at a certain time interval; it may also let them gain remote access to the system, which could be later used as an entry point into the network of the smart building.
Searching for exposed Philips Hue systems on Shodan retrieved 9,300 devices, a large deal of them using the insecure HTTP protocol.
Forescout’s case study applies not only to smart buildings but anywhere insecure protocols and vulnerable IoT devices are employed without making sure that the impact of compromising them does not extend to critical areas of the network.
Network segmentation, taking advantage of the security settings supported by the device, and authentication for devices that connect to the network are some of the ways to ensure a more secure digital perimeter.
More details of the research are available in Forescout’s paper titled “Rise of the Machines: Transforming Cybersecurity Strategy for the Age of IoT” and will be presented at the IoT Village event during the DEF CON 27 hacking conference.
In the video below, the researchers show how they were able to hijack the video feed of their test surveillance system.