
Attackers are deleting files on publicly accessible Lenovo Iomega NAS devices and leaving ransom notes behind. These ransom notes state that the attackers will give the files back if a bitcoin ransom is paid.
In a topic in the BleepingComputer forums, users are reporting that all of the files on their Lenovo Iomega NAS devices have been deleted or hidden and a ransom note was left in their place. This ransom note is named YOUR FILES ARE SAFE!!!.txt and state that the user’s files have been encrypted and moved to a safe location.
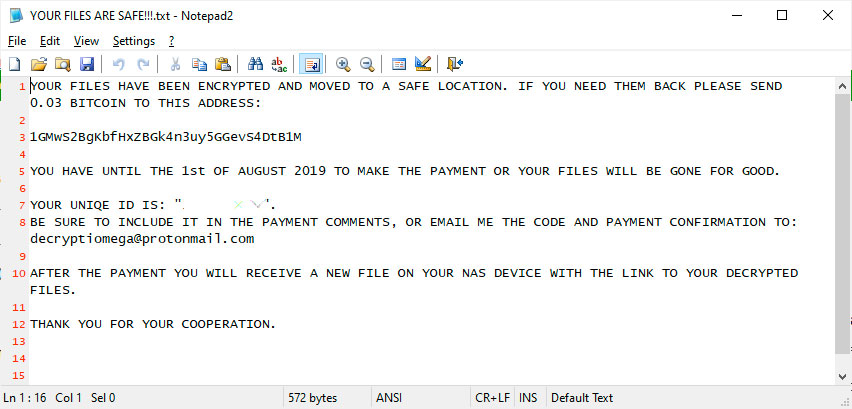
From the ransom notes seen by BleepingComputer, they are being created with different ransom amounts and messages. The most common message is that the user must pay 0.01 to 0.05 bitcoins to the specified address or the files “will be gone for good”.
YOUR FILES HAVE BEEN ENCRYPTED AND MOVED TO A SAFE LOCATION. IF YOU NEED THEM BACK PLEASE SEND 0.03 BITCOIN TO THIS ADDRESS: 13gMN3sJFxoLvoDzyGxq31sr4k9P2qqMDQ YOU HAVE UNTIL THE 1st OF AUGUST 2019 TO MAKE THE PAYMENT OR YOUR FILES WILL BE GONE FOR GOOD. YOUR UNIQE ID IS: "xxx". BE SURE TO INCLUDE IT IN THE PAYMENT COMMENTS, OR EMAIL ME THE CODE AND PAYMENT CONFIRMATION TO: iomega@cock.li AFTER THE PAYMENT YOU WILL RECEIVE A NEW FILE ON YOUR NAS DEVICE WITH THE LINK TO YOUR DECRYPTED FILES. THANK YOU FOR YOUR COOPERATION.A different variant that is less commonly seen warns that if the user does not make the payment, their files will be sold on the dark web.
YOUR FILES HAVE BEEN ENCRYPTED AND MOVED TO A SAFE LOCATION. IF YOU NEED THEM BACK PLEASE SEND 0.01 BITCOIN TO THIS ADDRESS: 172bnrSX351TEEVrFJTPAA9ktBxfjnweLm YOU HAVE UNTIL THE 15th OF AUGUST 2019 TO MAKE THE PAYMENT OR YOUR FILES WILL BE SOLD ON THE DARK WEB. YOUR UNIQE ID IS: "xxx". BE SURE TO INCLUDE IT IN THE PAYMENT COMMENTS, OR EMAIL ME THE CODE AND PAYMENT CONFIRMATION TO: decryptiega@protonmail.com AFTER THE PAYMENT YOU WILL RECEIVE A NEW FILE ON YOUR FTP DEVICE WITH THE LINK TO YOUR DECRYPTED FILES. THANK YOU FOR YOUR COOPERATION. One of the bitcoin addresses associated with this attack is 13gMN3sJFxoLvoDzyGxq31sr4k9P2qqMDQ and has received 9 payments since June 27th that could be related to this campaign based on the payment amounts.
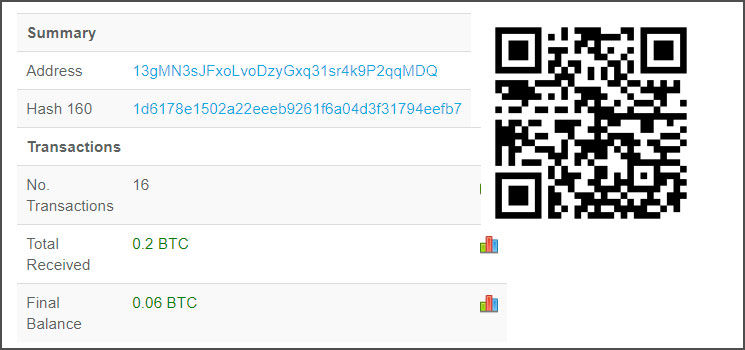
It is not known if the attackers restore the files after a payment has been made.
Files are deleted, but can be recovered
In conversations with victims, BleepingComputer has learned that the files are being deleted rather than encrypted and hidden somewhere on the drive.
As these are NAS devices with ext2 filesystems, some users have reported difficulty using file recovery software to work with the NAS devices.
One victim, though, has told BleepingComputer that they have had success using file recovery software after attaching the NAS device to their PC via a USB port.
Possibly gaining access via web interface
It is not clear how attackers are gaining access to the victim’s devices, but searches on Shodan show numerous Iomega NAS devices connected directly to the Internet.
Research by BleepingComputer shows that unsecured Iomega devices have publicly accessible front ends that allow you to remotely access your files over the web. If not properly secured, this web interface can allow a remote user to upload and delete folders from the NAS.
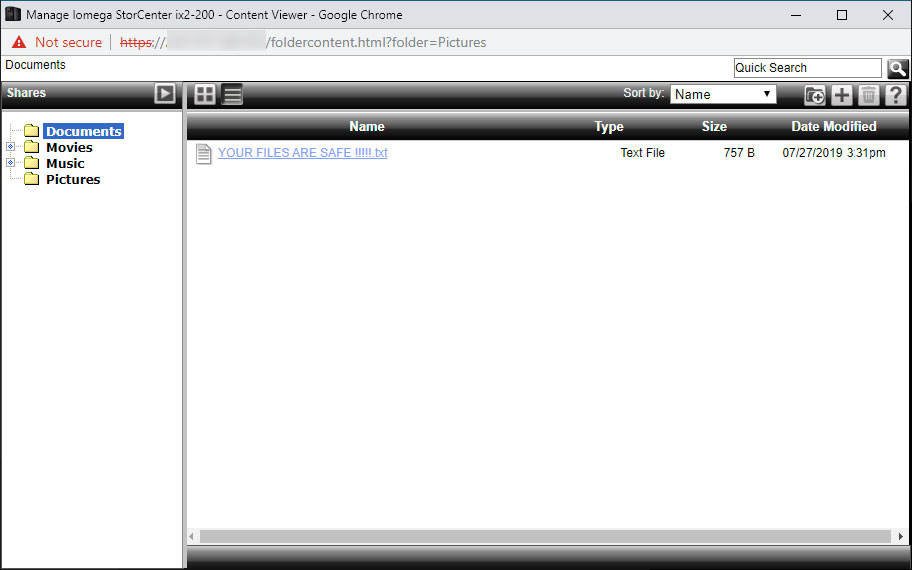
One of the victims told BleepingComputer that their Iomega NAS devices front end was not locked down and publicly accessible and may have been used as part of this attack. You can see an example of their web interface displaying the ransom note in their pictures folder.
Lenovo had released an advisory in the past on how to properly secure this interface that all owners should follow.
BleepingComputer has contacted Lenovo to see if they had further information, but had not heard back from them at this time.
Qnap and Synology NAS devices under attack as well
Iomega NAS devices are not the only ones being targeted by attacks that ransom victim’s files.
Just recently we reported on a new eCh0raix ransomware targeting QNAP NAS devices. After numerous users first reported this infection in our forums and further research was released, QNAP issueed an advisory on how to lockdown and secure their NAS devices.
Synology also released an advisory recently due to users reporting that their NAS devices were being infected by ransomware after attackers brute-force the passwords of their devices
Unless you require public access to your files, all NAS devices should be secured by a firewall and only accessible via a VPN. If you do not have the capability of using a VPN to access your internal network, then at a minimum you should make sure to secure the devices so that they require a strong password access the device.
H/T: Amigo-A
Thanks to @da_667 for the link on securing Lenovo NAS devices.
Related Articles:
No More Ransom Success Story: Saves $108+ Million in Ransomware Payments
Monroe College Hit With Ransomware, $2 Million Demanded
New eCh0raix Ransomware Brute-Forces QNAP NAS Devices
New Android Ransomware Uses SMS Spam to Infect Its Victims
The Week in Ransomware – July 26th 2019 – State of Emergency