
Now that ransomware developers know that they can earn monstrous payouts from local cities and insurance policies, we see a new government agency, school district, or large company getting hit with a ransomware attack every day.
For example, this week the Governor of Louisiana declared a state of emergency for the wave of attacks targeting school districts in the state.
Sodinokibi also continues to rear its head this week with a new campaign where they were impersonating Germany’s BSI. Otherwise, it has been a steady stream of new variants of existing ransomware and a smattering of new lower end families being discovered.
The good news is that a decryptor for the LooCipher Ransomware was released, which allows those victims to recover their files for free.
Contributors and those who provided new ransomware information and stories this week include: @demonslay335, @LawrenceAbrams, @malwrhunterteam, @Seifreed, @DanielGallagher, @PolarToffee, @struppigel, @BleepinComputer, @fwosar, @FourOctets, @malwareforme, @jorntvdw, @serghei, @Ionut_Ilascu, @FraMauronz, Emsisoft, @VirITeXplorer, @petrovic082, @thyrex2002, @CRN, @Malwarebytes, @GrujaRS, @JakubKroustek, @pollo290987, @1ZRR4H, @tribstar, @nhregister, @tcatshelbyville, @RecordedFuture, @certbund, @BSI_Bund, @malkoegler, @Europol, and @WHAS11.
July 20th 2019
New Scarab Ransomware variant
Alex Svirid found a new Scarab Ransomware variant that appends the {Help557@cock.li}.exe extension to encrypted file names.
LilLocked Ransomware found
Michael Gillespie is looking for a ransomware that appends the extension .lilocked and drops a ransom note named #README.lilocked.
Haka Ransomware found
Michael Gillespie is looking for a ransomware that appends the extension .haka and drops a ransom note named !!!READ_ME_FIRST!!!.txt.
New Tocue STOP Ransomware variant
Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .tocue extension to encrypted files.
July 21st 2019
New Daris STOP Ransomware variant
Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .daris extension to encrypted files.
STOP DJvu Ransomware decryptor updated
Michael Gillespie updated his STOP Decryptor to support the offline keys for the .gusau, .madek, and .tocue extensions.
New RotorCrypt Ransomware
Michael Gillespie found a new RotorCrypt Ransomware !-information-…___ingibitor366@cumallover.me___….RT4BLOCK and drops a ransom note named NEWS_INGiBiToR.txt.
New Lucky Joe Ransomware
Germán Fernández found a new ransomware called Lucky Joe that appears to be a GonnaCry variant. According to pollo290987, this variant drops a ransom note named GNNCRY_Readme.txt.
July 22nd 2019
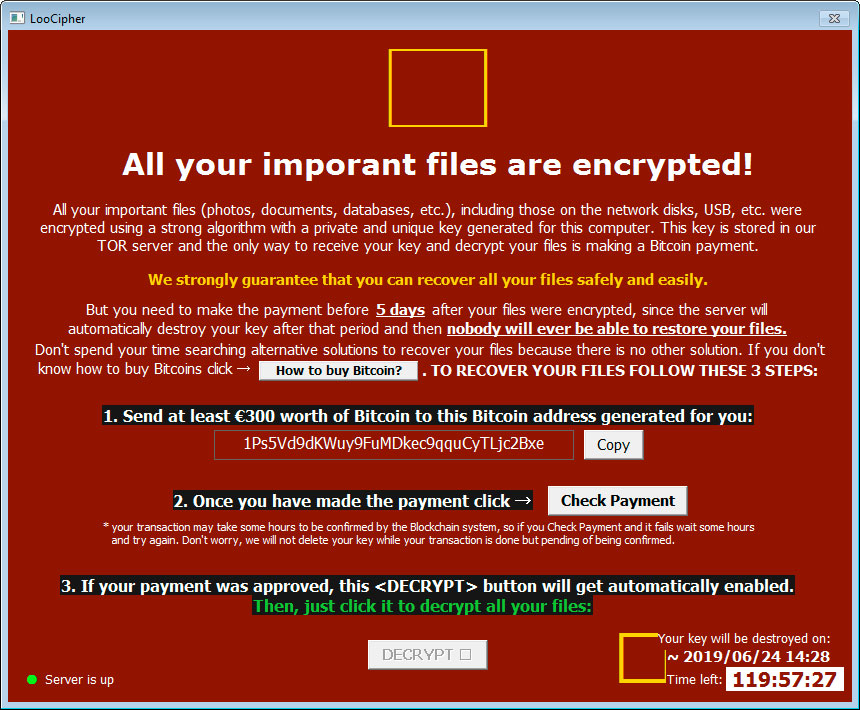
LooCipher Ransomware Decryptor Gets Your Files Back for Free
A decryptor for the LooCipher Ransomware has been released by Emsisoft that allows victims to decrypt their files for free. If you were infected with LooCipher, do not pay the ransom and instead follow the instructions below.
New STOP Ransomware variants
Michael Gillespie found new STOP Djvu Ransomware variants that append the .lapoi or .todar extension to encrypted files.
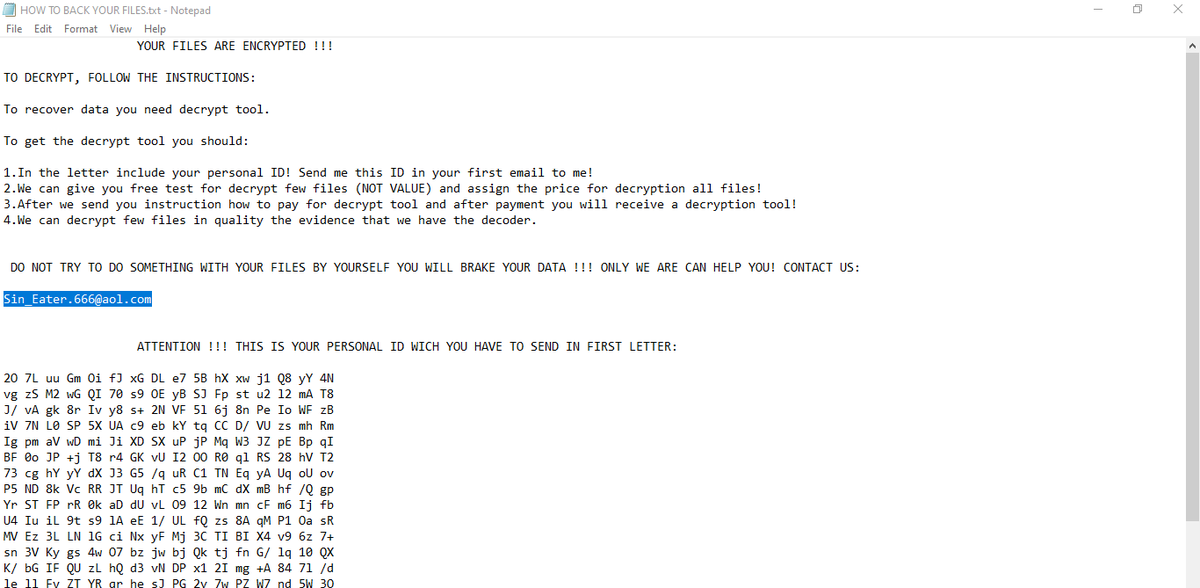
New Maoloa Ransomware variant
GrujaRS found a new Maoloa Ransomware variant that appends the .Hades666 extension and drops a ransom note named HOW TO BACK YOUR FILES.txt.
July 23rd 2019
Technical analysis of Ryuk ransomware that targets the large organizations
Ryuk ransomware, a modified version of Hermes, is used by Grim Spider a cyber-criminal group, it made its first appearance in August 2018.
New Dodoc STOP Ransomware variant
Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .dodoc extension to encrypted files.
New com2 Dharma Ransomware variant
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .com2 extension.
New ransomware taunting Emsisoft
A new ransomware was discovered by Petrovic that appears to be taunting Emsisoft by using the extensions .xuy and ..emsisosisoft.
Vigo County works to assess extent of malware attack
Vigo County officials are working today to determine what kind of attack was made on the county’s computer system.
July 24th 2019
Sodinokibi Ransomware Distributed by Hackers Posing as German BSI
BSI, the German national cybersecurity authority, has issued a warning regarding a malspam campaign that distributes the Sodinokibi ransomware via emails designed to look like official BSI messages.
Ransomware: Most Popular Malware in Underground Forums
Through the analysis of over 3.9 million posts on underground hacker and malware forums, a new report illustrates the most common malware and threats being discussed.
New STOP Ransomware variants
Michael Gillespie found new STOP Djvu Ransomware variants that append the .novasof or .bopador extensions to encrypted files.
NinjaRMM Partner Used To Seed Ransomware
NinjaRMM said its tool was used to spread ransomware across “multiple endpoints” within the last 36 hours, and it is encouraging partners to enable two-factor authentication, which it said could have stopped the attack, according to an email it sent to partners today.
A deep dive into Phobos ransomware
Phobos ransomware appeared at the beginning of 2019. It has been noted that this new strain of ransomware is strongly based on the previously known family: Dharma (a.k.a. CrySis), and probably distributed by the same group as Dharma.
An interview with Fabian Wosar, EMSISOFT’s ransomware killer
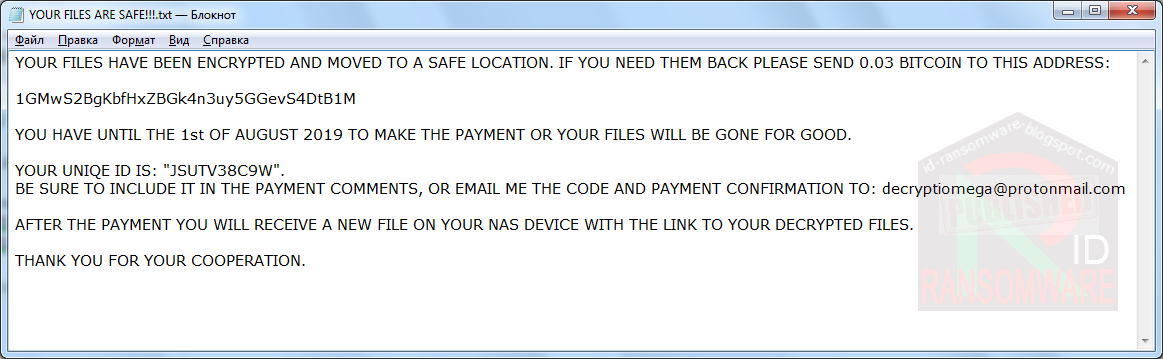
DecryptIomega Ransomware discovered
Amigo-A found a new ransomware called DecryptIomega that is target Lenovo Iomega NAS drives. The files are hidden, or removed, so it is not know if anything is encrypted, but it does drop a ransom note named YOUR FILES ARE SAFE!!!.txt.
New Haven Public Schools hit by ransomware attack
The New Haven Public School district recently was hit by a ransomware attack, an official confirmed Wednesday.
July 25th 2019
Ransomware Attacks Prompt Louisiana to Declare State of Emergency
Louisiana Governor John Edwards has declared a state of emergency after a wave of ransomware attacks targeted school districts this month. This Emergency Declaration will allow Louisiana state resources and cybersecurity experts to assist local governments in securing their networks.
Ransomware Attack Cripples Power Company’s Entire Network
A ransomware attack that hit the South African electric utility City Power from Johannesburg this morning encrypted all its systems, including databases and applications.
New Banjo Phobos Ransomware variant
Michael Gillespie found a new Phobos Ransomware variant that appends the .banjo extension.
New Ntuseg STOP Ransomware variant
Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .ntuseg extension to encrypted files.
STOP DJvu Ransomware decryptor updated
Michael Gillespie updated his STOP Decryptor to support the offline keys for the .lapoi, .todar, .dodoc, .bopador, and .novasof extensions.
New Acuf2 Dharma Ransomware variant
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .Acuf2 extension.
Ransomware attacks four Louisville healthcare clinics
Four Louisville healthcare centers are infected with ransomware, according to Park DuValle Community Health Center CEO Ann Hagan-Grigsby. This is the second attack so far this year. The CEO said they contacted the FBI shortly after learning of the infected servers.
July 26th 2019
No More Ransom Success Story: Saves $108+ Million in Ransomware Payments
Today marks the third anniversary of No More Ransom and through its partners from the public and private sectors, law enforcement, academia, and researchers, the project has been able to help hundreds of thousands, if not millions, of victims get their encrypted files back for free.
New Ndarod STOP Ransomware variant
Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .ndarod extension to encrypted files.
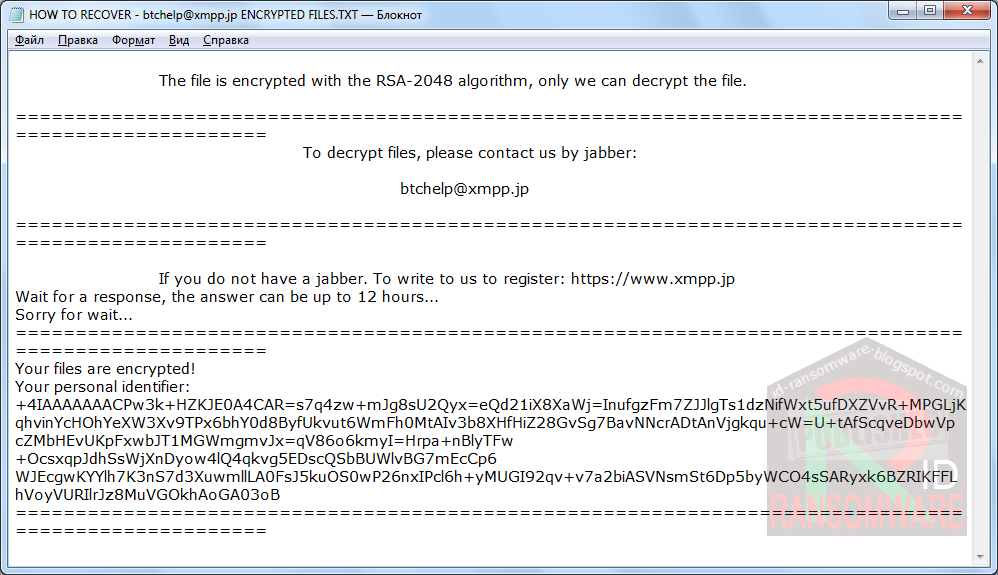
New Scarab Ransomware variant
Amigo-A found a new Scarab Ransomware variant that appends the .btchelp@xmpp.jp extension to encrypted files and drops a ransom note named HOW TO RECOVER – btchelp@xmpp.jp ENCRYPTED FILES.TXT.
That’s it for this week! Hope everyone has a nice weekend!
Related Articles:
The Week in Ransomware – July 19th 2019 – Targeted Attacks
The Week in Ransomware – July 5th 2019 – Shadiness in the Sunshine State
The Week in Ransomware – June 21st 2019 – Backup, Backup, Backup!
Ransomware Attacks Prompt Louisiana to Declare State of Emergency
Ryuk, Sodinokibi Ransomware Responsible for Higher Average Ransoms