
Open Wi-Fi Credential Harvesting With IoT
Open Wi-Fi Credential Harvesting With IoT
IoT poses a serious threat to public Wi-Fi networks.
Mar. 25, 19 · IoT Zone ·
Comment (0)
Join the DZone community and get the full member experience.
Download The Comparative Guide to Rules Engines for IoT to learn what are the most common automation technologies used in the IoT domain for application development

Free, open Wi-Fi connections sound tempting, but are they actually free? Perhaps, instead of monetary payments, these open Wi-Fi networks are costing you something else — your identity.
Imagine you are waiting at an airport with a five-hour layover until your next flight. While bored and having nothing to do, you pick up your phone to idly scroll Facebook and Instragram to pass the time. However, you soon realize that it’s not so fun without an Internet connection. This reminds you to check to see if there are any free Wi-Fi connections. And boom, there are several free, open Wi-Fi connections hosted around the airport. Without thinking twice about it, you connect to a Wi-Fi network — after filling out a quick form asking for your passport number, name, flight details, etc. Or maybe, you are prompted for your email or Facebook credentials.
Congratulations! You just threw away your identity all for just a few mega bytes of Internet.
Open Wi-Fi connections have been considered a security nightmare since the beginning. But because there are no easy alternatives, open Wi-Fi connections still remain widely used in most public locations, such as coffee shops, airports, etc.
Traditional, open Wi-Fi hacking involves a bit of manual work. Hackers need to perform MITM attacks usually with ARP Poisoning. Since websites, nowadays, are channel-encrypted, this involves more work like "SSL striping" to get the most out of it. This is doable but not practical — since we can conduct credential harvesting through this approach.
With the development of IoT, there are disturbingly easy ways for credential harvesting on a public Wi-Fi connection. In this article, I’m going to explain a simple POC to further explain the dangers that IoT brings to open Wi-Fi connections.
Device Used for the POC: ESP8266

With latest trends in IoT, there’s a huge demand for low power/low cost SoC (system on chip) with build-in connectivity features. Esp8266 was manufactured by "Espressif Systems" to cater this gap back in 2013. It soon gained popularity amongst IoT enthusiasts and other businesses.
Esp8266 supports TCP/IP stack apart from it’s microcontroller capabilities. The main advantage of this tiny/cheap chip is that it supports Wi-Fi connectivity with full TCP/IP stack and IEEE 802.11 b/g/n WLAN protocol. This opens up endless possibilities in IoT and hacking domains.
ESP8266 Feature Highlights
MCU: Tensilica Xtensa L106 — 80MHz(default mode) or 160MHz
External flash memory: 512 KB to 4 MB typically included in commercial variants. (supported upto 16MB)
Connectivity: Wi-Fi (IEEE 802.11 b/g/n)
RAM: 32 KB instruction RAM, 32 KB instruction cache RAM, 80 KB user data RAM
A quick search on shodan.io will show a number of esp8266 devices exposed on the Internet. Numbers are increasing as it’s gaining a huge popularity among IoT communities. There are various development boards released with this chip as well. Further, this chip is commonly available, starting from 2 USD on ebay.
I’m going to explain how two esp8266 devices can be used for open Wi-Fi credential harvesting attacks.
Step 1: De-Authenticate Connected Clients From Target Access Point(s)
First, the attacker needs to de-authenticate client devices connected (and connecting) to free Wi-Fi access points. Even though this step is not mandatory, it will increase the success rate of the attack.
In order achieve this, an attacker can exploit a major flaw in the IEEE 802.11 WLAN protocol prior to the IEEE 802.11w-2009 amendment. In early IEEE 802.11 specifications (prior to 2009), management frames (which are responsible to authenticate, maintain, and discontinue communication) are not protected from underlying encryption mechanism. This enables anyone within range of the target station to de-authenticate from the access point by sending de-auth frames to the target station.
If you are curious about these frames, you can use the following search filter in wireshark to filter de-authenticate frames. First, you need to put your Wi-Fi adapter in ‘monitor mode’ on a selected channel. Keep in mind, there are tons of tutorials out there how to monitor Wi-Fi packets using wireshark.
(wlan.fc.type == 0)&&(wlan.fc.type_subtype == 12)(wlan.fc.type==0): Filter 802.11 management frames
(wlan.fc.type_subtype==12): Filter ‘de-authenticate’ frames (subtype 12)
If you open up the ‘monitor mode’ for all the channels, and in a congested area with lots of wireless devices, you’ll soon capture de-auth frames through wireshark.
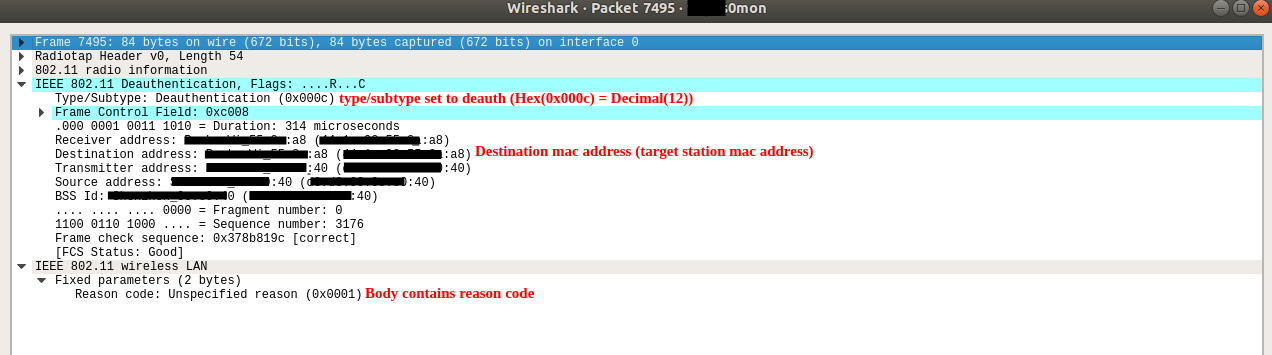
If an attacker can replay these de-auth frames continuously to a router or client station, it will fail to establish successful authentication. This vulnerability has already been fixed in the IEEE 802.11 protocol for protected access points back in 2009. But as Wi-Fi access points need to be backward compatible with old IEEE 802.11 specifications, this vulnerability still remains intact in all most all commercial routers. Further, in this scenario, Wi-Fi traffic won’t get encrypted as long as Wi-Fi connections are open. Therefore, management frames will remain unprotected in open Wi-Fi connections despite the IEEE 802.11 2009 amendment.
ESP8266-Based Wi-Fi Deauthenticator
I’m not going to do a step-by-step walkthrough on how to create a ESP-based deauthenticator. As there’s a well documented open-source project and many online tutorials how to use esp8266 since there is a Wi-Fi deauthenticator based on above-mentioned vulnerability.
Unlike a Wi-Fi jammer, which adds noise to Wi-Fi communication frequencies (which disable all Wi-Fi communication within range), with this approach, attackers can disable given target access points, for example, open Wi-Fi access points, as required.
Step 2: Pretend to Be the Public Wi-Fi Captive Portal
When a user can’t make a successful connection to a legit open Wi-Fi access point, they will eventually attempt other available Wi-Fi options. Now, the attacker just needs to host an open Wi-Fi access point with spoofing captive portal to harvest credentials from the target audience.
ESP8266-Based Captive Portal Server
Esp8266 can act as a fully capable REST compliant server. For a single chip system, this is pretty amazing. For just little as 2USD, now you can get device powerful enough to host several web services. With some fiddling, I was able to develop POC captive portal server, which supports the following features:
- Captive portal, which supports multiple platforms (Windows, Ubuntu, Android)
- DNS server to spoof any inbound traffic
- Handle HTTP rest requests and mechanism to stream resources to client
- Use built-in SPIFFS memory to store web pages (with js and CSS support)
- Write inputs from client to SPIFFS (on REST post request from client)
- Access and manage SPIFFS memory remotely.
Quick Demo
1. Here is a captive portal initial login page when it connects to a Wi-Fi access point:

2. SSO(single sign-on) style credential spoofing

This is just a POC, and Facebook login is nothing like the actual Facebook login UI. Adding a convincing UI with proper JavaScript validations is really easy — as all those are done from client device. Esp8266 just needs to stream the HTML, CSS, and JavaScript resources when requested by a client.
Additionally, credentials can be validated by an actual sso implementation with the identity provider as well. If provided credentials are invalid, the login failure flow can be implemented.
3. Settings page for maintenance:

Hackers can do all maintenance and credential collections remotely by connecting just as another client. Since esp8266 has limited memory(4MB), the data needs to be collected and clear before the data file grows beyond memory limits.
This can be further improved by adding a simple monitor to the data file size and uploading the file if the size exceeds a certain limit. With this, a hacker won’t have any direct involvement with the device as well.
Another major advantage of esp8266 is that it can act as a dns server. Therefore, it can mimic any hostname(ex: www.facebook.poc.com). For the sake this POC, all requests were routed to "192.168.1.1," regardless of the hostname.
I’m not going to walk-through the code base and implementation as it will make this article unnecessarily lengthy. Project files can be found in my Git repository for reference.
The scariest part is that hackers don’t have to click a single button to perform this type of attack. The hacker just needs to prepare both esp8266 devices (step1: deauthenticator and step 2: captive portal server) and place them securely near the target audience. Thanks to esp8266 low power consumption, it will last weeks, or maybe months, without any need of a battery replacement.
Conclusion
ESP8266 is certainly not the the only SoC device that is capable of this type of attack. But it’s the easiest attack with minimum cost and effort. Further, manufacturers are developing new advanced SoCs with much higher capabilities. For example, esp32 was released back in 2016. It’s the successor of esp8266, which contains Bluetooth, in addition to Wi-Fi connectivity.
With the advancement of IoT devices, there are silent security threats that can emerge out of nowhere. Users no longer have the privilege to shut off from security aspects, thinking no one will ever be interested in their identity — unless they want some random hacker selling their identity along with thousands of other harvested credentials in dark web to some unknown party.
See how CEP engines, stream processing engines, flow based programming engines and other popular rule-based technologies perform against seven IoT-specific criteria.
Like This Article? Read More From DZone
Comment (0)
Published at DZone with permission of Pumudu Ruhunage . See the original article here.
Opinions expressed by DZone contributors are their own.
IoT Partner Resources
IoT Partner Resources
- {{ node.blurb }}
{{ editionName }}
{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}





